
Introduction
Web3 & Blockchain Consultancy :
SHA-256 Hash Algorithm: How Does It Safeguard Digital Transactions?
Security is a paramount concern in the digital world, particularly when conducting digital transactions. In 2024, the rise of fundamental technology SHA-256 Algorithm made digital transactions secure. This sha256 hashing algorithm ensures the integrity and security of these transactions is the SHA-256 algorithm. As a cryptographic function, it is important for various security protocols, including those used in secure web browsing, digital signatures, and blockchain technology. This guide will work as a detailed exploration to provide you with a comprehensive understanding of SHA-256 hashing, its mechanics, applications, and its indispensable role in modern cybersecurity.Overview of SHA-256 Hashing Algorithm
SHA-256 or Secure Hash Algorithm 256-bit both are the same terms. It is a part of the SHA-2 family of cryptographic hash functions designed by the National Security Agency (NSA) and published in 2001. The function converts an input of any size into a fixed 256-bit output in a one-way process, which means the original data cannot be feasibly retrieved from the output hash. This characteristic is important to protect data integrity and to prevent unauthorized data manipulation.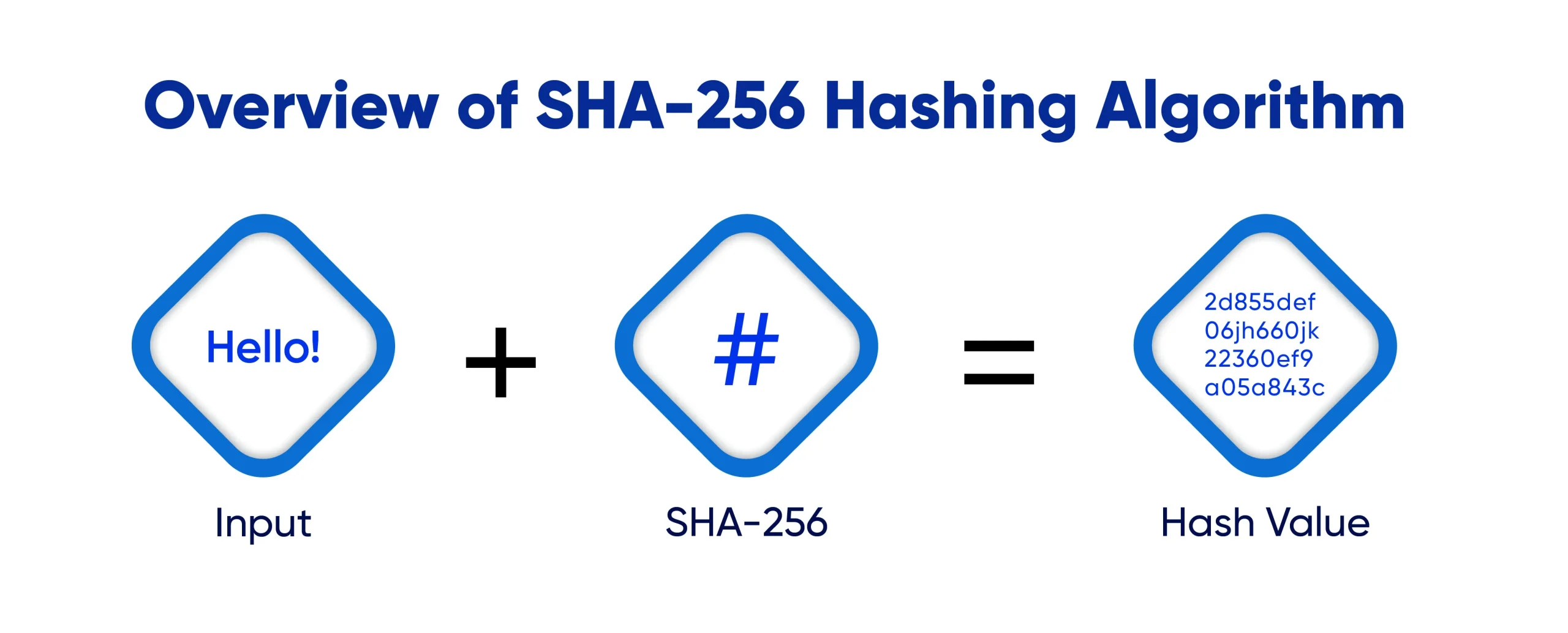
Characteristics of the SHA-256 algorithm
The SHA256 hashing algorithm has several notable features, including message length, being irreversible, and digest length. It means the cleartext should be less than 264 bits. The size must be in the comparison range to keep the digest as random as possible. The hash digest should be 256 bits for the SHA-256 algorithm, 512 bits for SHA-512, and so on. Larger digests typically indicate significantly more calculations at the expense of speed and space. All hash functions, including the SHA 256, are irreversible. You should not get a plaintext when you already have the digest, nor should the digest provide its original value when you pass it through the hash function again.How Does the SHA-256 Algorithm Work?
SHA-256 hashing follows a complex yet thoroughly secure process to ensure that even a small change in the input will result in a drastically different output, thereby safeguarding against duplications and tampering: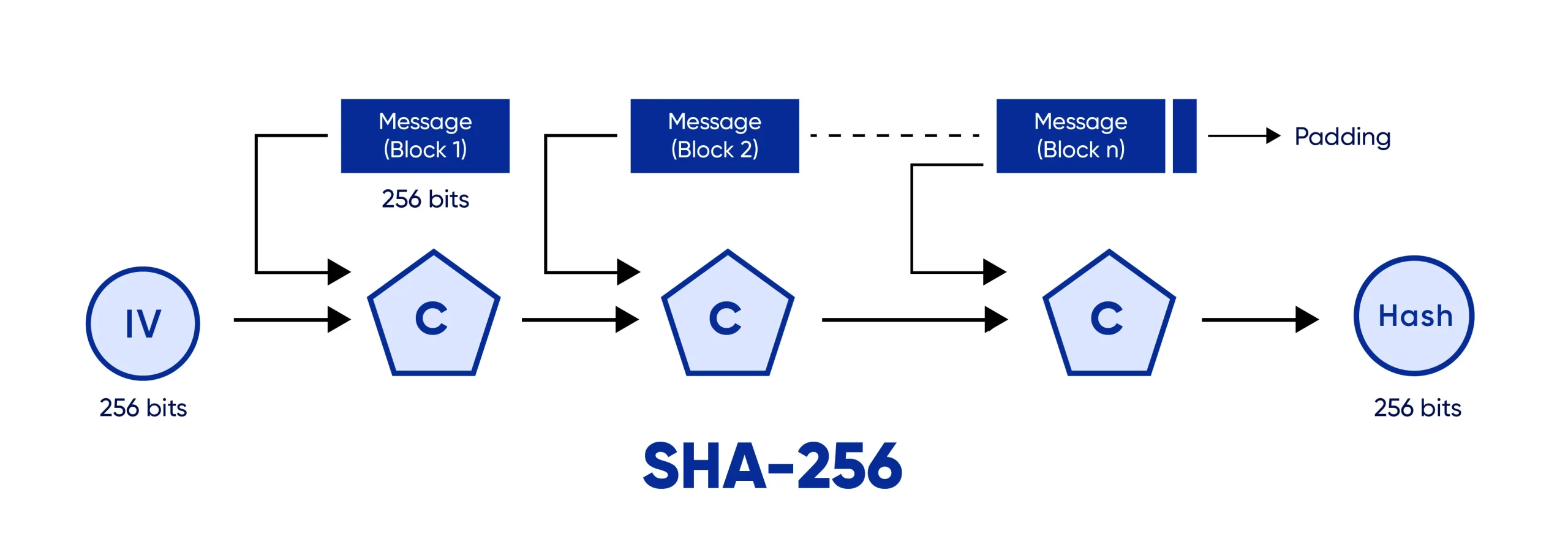
- Padding and Parsing: Initially, the input data is prepared by padding it to ensure its length is a multiple of 512 bits. This padding includes appending a ‘1’ followed by ‘0’s and then the original length of the message.
- Setting Up the Hash Computation: The SHA-256 algorithm uses a set of initialized values derived from the fractional parts of the square roots of the first eight prime numbers. These are part of the algorithm’s compression function that processes the data.
- Block Processing: Each 512-bit block of the data is processed through a series of 64 iterations known as rounds. During these rounds, the data is mixed and combined in various sophisticated ways involving bitwise operations, modular additions, and compressions, which are based on predefined constants and functions.
- Final Hash Generation: The processed blocks are then combined to produce the final SHA-256 hash. This resultant hash is unique to the specific input data, fulfilling its role as a digital fingerprint.
Applications of SHA-256 Hashing in Digital Transactions
SHA-256 (Secure Hash Algorithm 256-bit) is widely used in digital transactions and cryptographic applications due to its properties of generating unique fixed-size hash values that are computationally infeasible to reverse-engineer. Here are some specific applications of SHA-256 hashing in digital transactions:
- Digital Signature Verification: SHA-256 is extensively used to generate digital signatures. It hashes a document or data, and then the hash is encrypted with a private key to create a signature. This signature helps verify the integrity and authenticity of the message or document.
- Password Hashing: Websites store user passwords in a blockchain hash format for two benefits. It helps foster a sense of privacy, and it lessens the load on the central database since all the digests are of similar size.
- Blockchain Technology: SHA-256 is a critical component in the operation of blockchain networks, such as Bitcoin. It is used to hash transaction data into a consistent and secure format that is then inscribed into each block of the blockchain, ensuring the security and continuity of the ledger.
- SSL/TLS Certificates: In the context of SSL (Secure Sockets Layer) and TLS (Transport Layer Security), SHA-256 ensures that the certificates used to secure a web connection are authentic and have not been tampered with, thereby securing blockchain data transferred over these connections.
- Integrity Checks: Verifying file integrity has been using variants like the SHA 256 algorithm and the MD5 algorithm. It helps maintain the full value functionality of files and makes sure they were not altered in transit.