
Introduction
Blockchain & Web3 Services Trusted By Leaders
- Develop innovative solutions using our state-of-the-art blockchain expertise.
- Achieve accelerated growth with robust & scalable Web3 consulting.
- Unlock 360-degree security with our top-rated blockchain development.
Symmetric Vs Asymmetric Encryption: What’s Best for Maximum Security?
The concept of encryption comes from popular culture like the TV show “Mr. Robot” in which they use asymmetric encryption to protect data from hacking. As a result, encrypting data and blockchain cybersecurity becomes important for businesses, organizations, governments, and individuals. However, encrypting data involves choosing between types of encryption; symmetric vs asymmetric encryption. Each has its advantages and disadvantages but the choice depends on factors like data nature, security level, performance, and cost implications, making it a difficult decision. This blog will explore symmetric vs asymmetric encryption, types of encryption, and the difference between symmetric and asymmetric encryption;What is Cryptography?
People think cryptography and data encryption are the same. But they are not, cryptography is a broader field that focuses on securing information through various techniques. These techniques involve;- Encryption (scrambling data to make it unreadable without a key)
- Decryption (unscrambling encrypted data back to its original form)
- Blockchain Hash (creating a unique fingerprint of data for verification)
- Digital signatures (verifying the authenticity and origin of data)
- Key management (securely generating, storing, and distributing keys)
What is Data encryption?
It is a specific technique within cryptography that focuses on transforming plain text into an unreadable format that is ciphertext using a secret key. Only someone with the correct key can decrypt the ciphertext back to plaintext.How Data Encryption Works?
Data encryption methods can protect data from unauthorized access and snooping. It involves the use of a cryptographic algorithm to encrypt and decrypt data. The encryption key is a random string of numbers, letters, and symbols that a cryptographic algorithm uses to encrypt and decrypt data. However, the strongest encryption keys are unique and unpredictable, and as long as current technology allows it, they remain unbreakable. The encryption algorithm transforms plaintext into ciphertext, making it appear random to unauthorized users but decipherable to the intended recipient. The decryption key then makes the encrypted data readable again.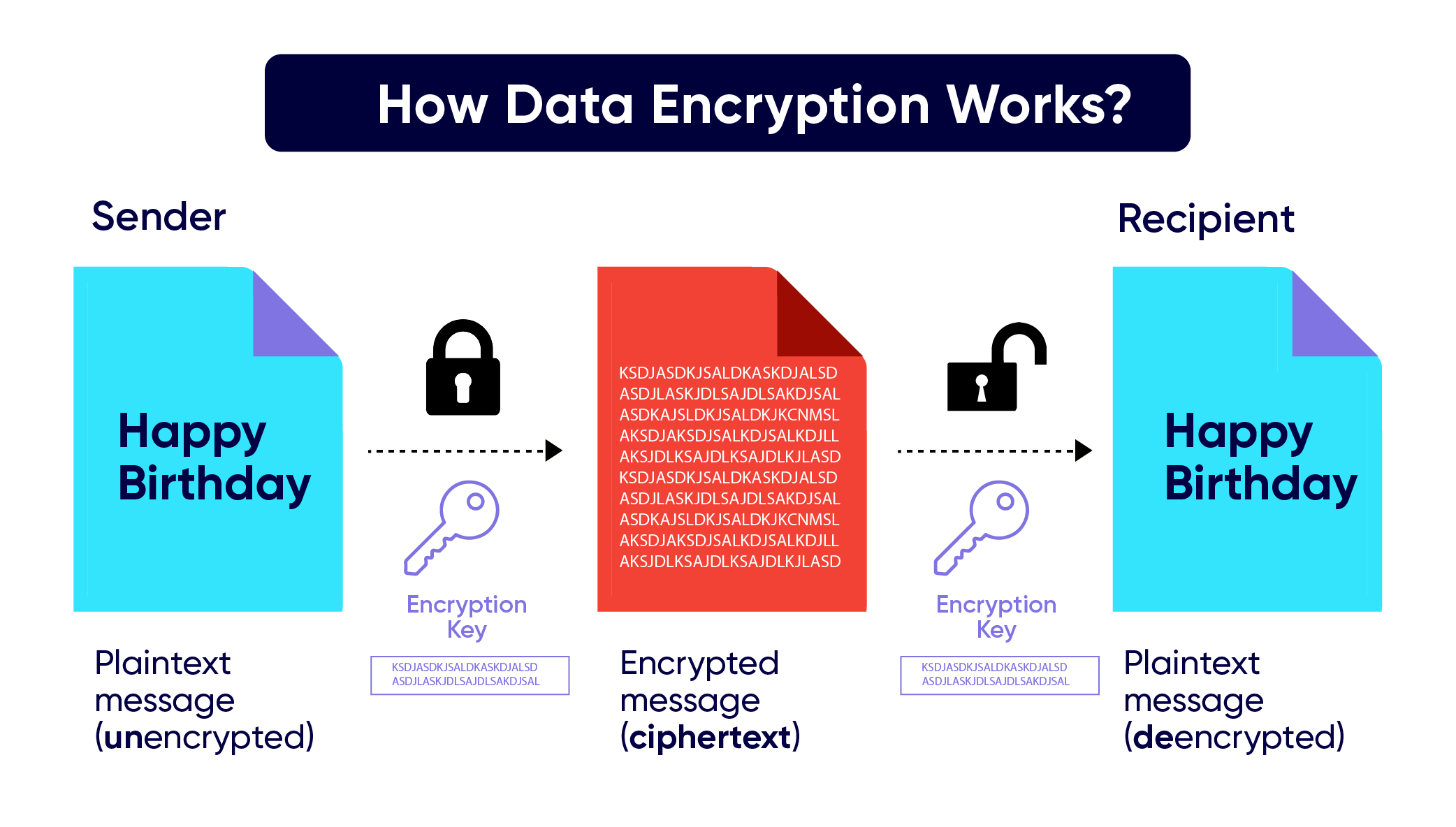
Why is Data Encryption Important?
Data Encryption is highly effective for some reasons. It protects confidential data such as passwords, social security numbers, and medical records. It also helps track real-time location and movements, including online and physical activities. Encryption also helps in reading conversations and altering their content, potentially leading to infected websites. Despite the risks, encryption is already used daily in various activities such as shopping online, sharing private messages, and transferring sensitive files.Types of Encryption Mechanisms
Different types of encryption algorithms and methods are available. But, how to pick the safest one for your cybersecurity needs? Let’s begin with the most common types of encryption systems: symmetric vs asymmetric encryption.What is Symmetric Encryption?
Symmetric encryption (AES) involves both sender and receiver using a symmetric (same) key for encrypting and decrypting messages. Key confidentiality is important, but the key distribution problem is a significant challenge. Loss or misplacement of keys can lead to malicious individuals decrypting messages. However, Symmetric encryption is considered faster than asymmetric encryption.What is Asymmetric Encryption?
Asymmetric encryption (RSA) is often known as public-key encryption. It is a method that works on three principles that are confidentiality, authenticity, and non-repudiation of electronic communications and data storage. RSA uses two keys that are different from each other. A private key and a public key, both of which are derived from long-length prime numbers. However, due to its mathematical complexity and computational power, asymmetric encryption is considered slow and not suitable for long sessions.Key Differences Between Symmetric and Asymmetric Encryption
Think of encryption as a silent guardian in the digital world. Scrambling data to safeguard its confidentiality and integrity. This complex task is only done by two main warriors: symmetric encryption and asymmetric encryption. While both strive for the same goal, they wield their power in distinct ways. Let’s check the key differences;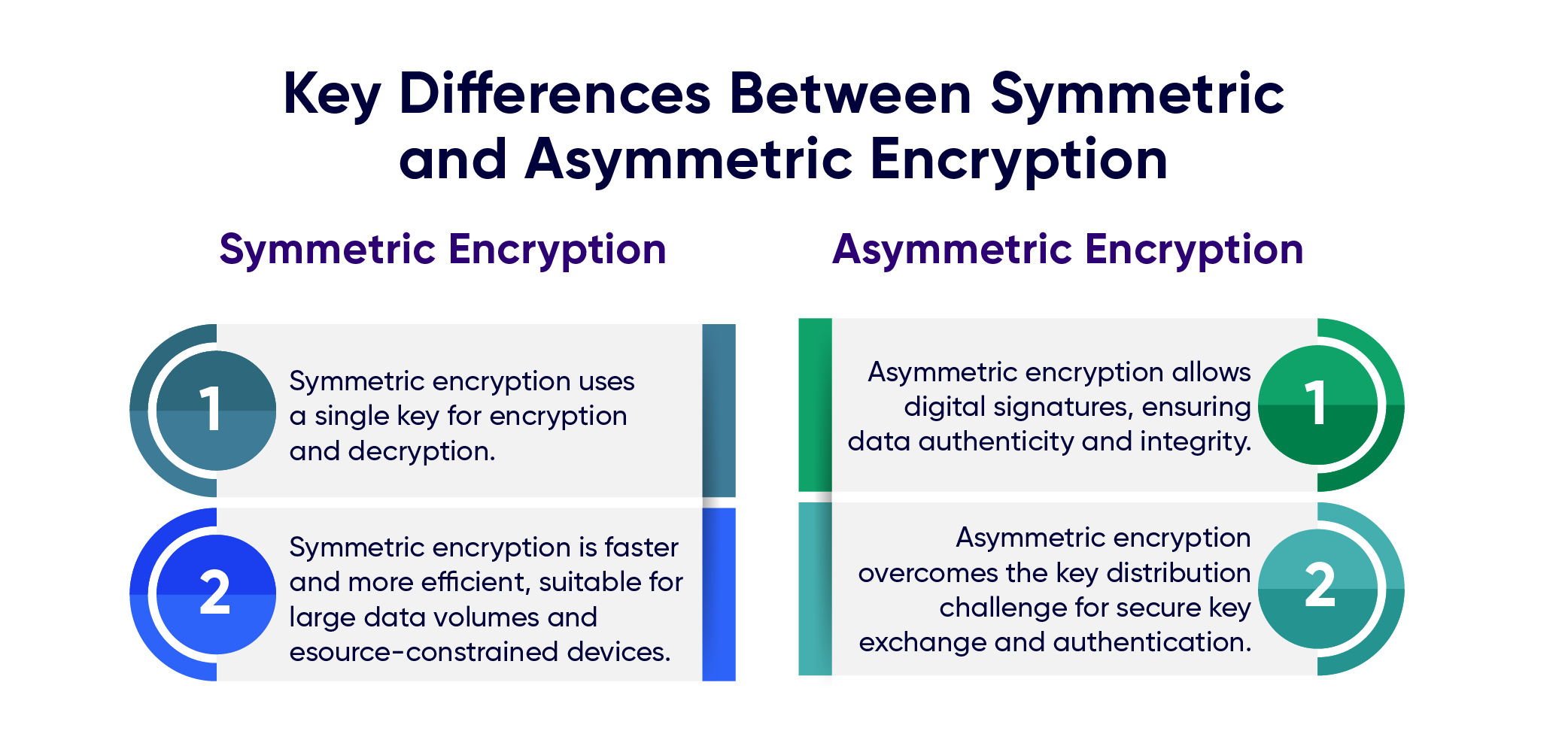
- Firstly, symmetric encryption is a fast and efficient way to encrypt large volumes of data. It is considered safe because of a single secret key used for both encryption and decryption. However, it is vulnerable due to the need for both the sender and receiver to possess the secret key securely, especially in untrusted online environments.
- Asymmetric encryption, on the other hand, employs a pair of mathematically linked keys, a public key, and a private key. The public key works as a widely distributed mailbox that allows anyone to use it to encrypt messages, while the blockchain private key serves as the personal key held confidentially by the recipient.
- Secondly, asymmetric encryption eliminates the key distribution challenge of symmetric encryption algorithms. It allows only the recipient with the house key to access the contents. It also empowers digital signatures, allowing the sender to verify the authenticity and integrity of a message.
- However, this robust security comes at the cost of speed. Asymmetric encryption is computationally more intensive, making it slower than its symmetric counterpart. However, for scenarios requiring secure communication and data integrity, such as signing financial transactions or verifying website identities, the added security outweighs the slight decrease in speed.
Symmetric Encryption Algorithms |
Asymmetric Encryption Algorithms |
| AES: A replacement for the outdated DES, designed to solve its main weakness of short encryption key length. | RSA: A staple of asymmetric encryption, designed by engineers in 1977, uses the factorization of the product of two prime numbers to deliver encryption of 1024-bits and up to 2048-bit key length. |
| 3DES: An advanced form of the deprecated DES algorithm, using a 56-bit key to encrypt blocks of data. 3DES is slower due to applying the same process three times to each block of information, and by using small blocks of data, the risk of brute force decryption is higher. | ECC: A method based on elliptic curves on a finite field, used to provide a security level of 256 bits at a maximum key length of 521 bits. ECC is considered the future of encryption, providing a security level of 256 bits at a maximum key length of 521 bits, ensuring fast encryption speeds with a high complexity of decryption. |
Symmetric Vs Asymmetric Encryption: What’s Best For Maximum Security?
The choice between symmetric and asymmetric encryption depends on specific security requirements and use cases. Understanding when to use symmetric or asymmetric encryption is vital for maintaining secure communications and protecting sensitive data. Factors like key management, computational efficiency, and desired functionality should be considered. Let’s see how you can select the right encryption methods by checking these factors according to your needs;- Symmetric and asymmetric encryption can maintain secure communications and protect sensitive data.
- Factors like key management, computational efficiency, and desired functionality should be considered.
- Symmetric encryption is ideal for handling large volumes of data due to its speed and efficiency.
- Asymmetric encryption is used for secure key exchange in protocols like SSL/TLS.
- Asymmetric encryption is suitable for creating digital signatures, allowing users to authenticate documents and verify their integrity.