
Introduction
Web3 & Blockchain Consultancy :
zk-SNARKs vs zk STARKS: A Comparative Analysis
Blockchain technology has transformed various industries including healthcare, supply chain, and finance, but scalability remains a significant hurdle. Popular platforms like Ethereum also face slow transaction processing and more gas fees. To address this challenge, zero-knowledge proofs (ZKPs) have emerged as a solution. They function as key players in the blockchain ecosystem by providing privacy and scalability. They generate proof – a computation that has a specific output while verifying transactions quickly and keeping some computation inputs hidden. ZK-SNARK is the most popular implementation of this cryptographic technology, but modern ZK-EVMs also employ zk-STARK for better efficiency. In this article, we will compare these two ZK protocols, zk-SNARKs vs. zk-STARKs, to make it clear, What benefits they provide to address blockchain’s scalability.What is ZKP or Zero Knowledge Proof?
Zero-knowledge-proof (ZKP) technology is a cryptographic protocol that allows one person (the prover) to verify a claim made by another without disclosing any supporting information. ZK must meet three requirements: Completeness, Soundness, and Zero-knowledge. However, there are two types of ZKPs, interactive and non-interactive. Interactive proofs involve repeated interactions between the prover and the verifier, while non-interactive proofs require a single transaction to verify the prover’s veracity. ZKPs ensure privacy and security of users’ information, such as confirming a payment recipient’s bank account balance without disclosing the payer’s balance.
What are ZK-SNARKs?
Zk-SNARKs or zero-knowledge SNARKs are a proof architecture that enables the demonstration of ownership of specific knowledge, such as a secret key. It does not disclose it or interact with the prover or verifier. This proof architecture is used in most cryptocurrencies to ensure specific requirements are met before validating a transaction, such as verifying the sender’s funds and providing the correct private key. This is what the computational values look like;How Does ZK SNARKs Work?
Zk-SNARKs transform information into equations during the transaction procedure. This process allows for the assessment and it solves these equations without revealing the actual data. However, Zcash was the first to apply zk-SNARKs to demonstrate transaction requirements without disclosing significant details. It is important to note that Zk-SNARKs have flaws, as anyone with the private key needed to set up the protocol could fabricate evidence and create fake money. Therefore, Zk-SNARK-based privacy coins must ensure no single party has access to the private key.What are ZK-STARKs?
Zk-STARKs also known as Zero-Knowledge Scalable Transparent Argument of Knowledge. This zero-knowledge is a transparent and scalable method to enhance privacy. The method also eliminates the need for a trusted setup. On the other hand, these cryptographic proofs enable users to communicate validated data or execute computations with a third party without the data or analysis being revealed.How Does ZK STARKs Work?
Unlike zk-SNARKs, which were used to build zk-proof systems, zk-STARKs distance away from the requirement for a reliable setup. STARKs helps improve scalability and privacy issues with permissionless blockchains. It enables developers to relocate computations and storage off-chain by producing STARK proofs that verify the accuracy of off-chain computations. They also enable existing blockchain infrastructure to scale exponentially without compromising computational integrity. In essence, Layer-2 solutions use zk-STARKs to compute thousands of transactions in a single batch, with all transactions sharing the cost of the on-chain operation.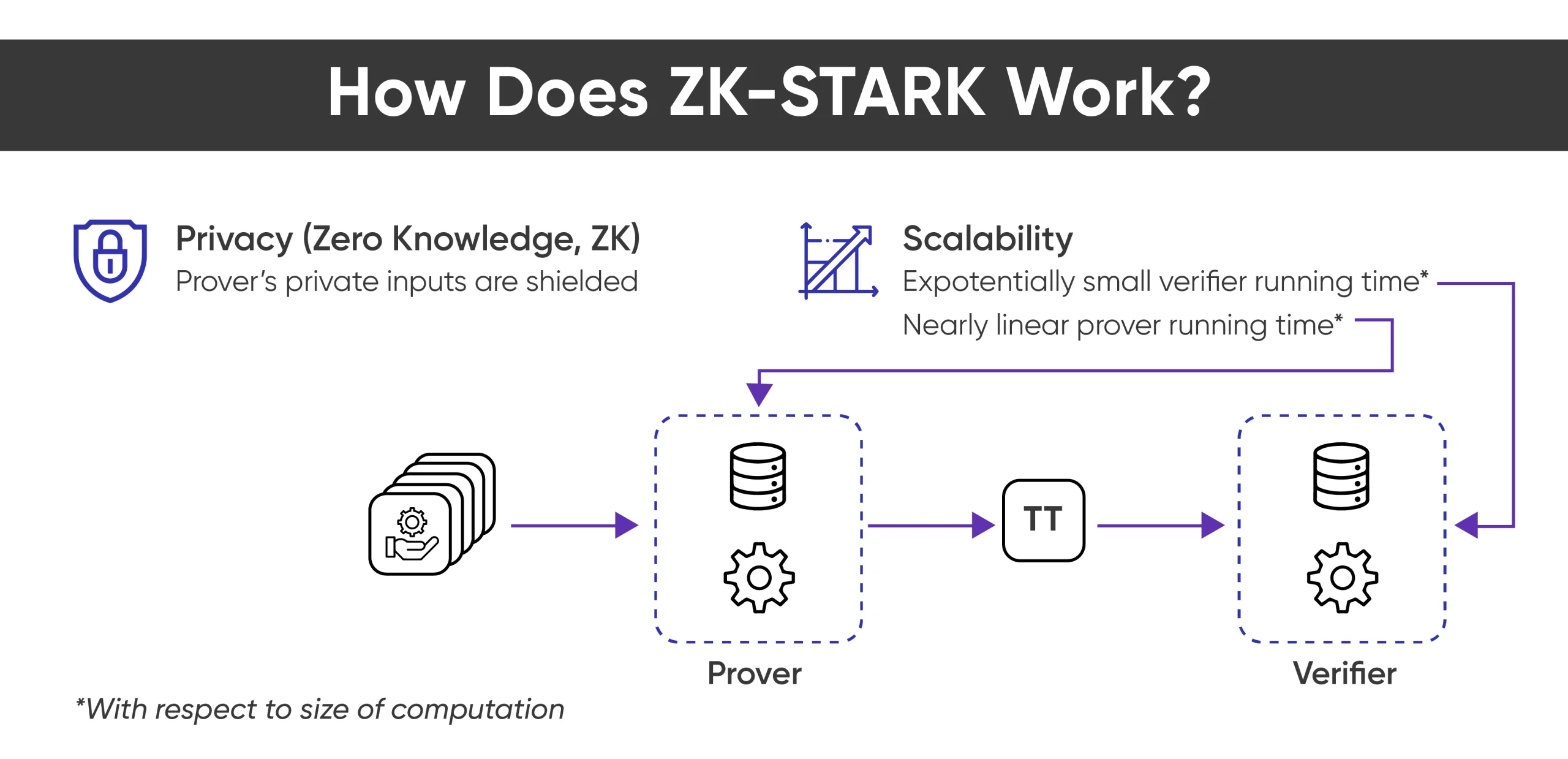
Key Differences: zk-SNARKs vs zk-STARKs
Zero-knowledge-proof technologies are used to enhance privacy and scalability. It allows proofs to be verified faster due to their lack of full information for non-private systems. Two of the most compelling zero-knowledge technologies are zk-STARKs, which stands for the zero-knowledge scalable transparent argument of knowledge, and zk-SNARKs, which stands for the zero-knowledge succinct non-interactive argument of knowledge. Both technologies differ from a cultural and technical perspective, as they are non-interactive, allowing code to act autonomously. Let’s explore the core differences between these two technologies;Feature: zk-SNARKs vs zk-STARKs
| Features | zk-SNARKs | zk-STARKs |
| Trusted Setup | Required | Eliminated |
| Verification Time | Faster (Potentially) | Fast |
| Implementation Complexity | Lower | Higher |
| Proof Size | Smaller | Larger but scalable |
| Quantum Resistance | Vulnerable | Resistant |
Key Differences Between zk-SNARKs and zk-STARKs
| Criteria | zk-SNARKs | zk-STARKs |
| Reliable Setup | A trusted setup ceremony is required for the initial parameters. Any vulnerabilities introduced at this stage could compromise the system’s overall security. | This kind of Zero Knowledge Proof eliminates the need for a trusted setup, resulting in a more secure and intrinsically trustless foundation. |
| Verification Time | Verification times can be faster than STARKs under specific conditions which can be beneficial for efficient transaction verification on blockchains. | The verification time of zk-STARKs is fast. The verification can be achieved more quickly under certain circumstances. |
| Implementation Complexity | As a more established technology, SNARKs have more mature libraries and tools readily available for implementation. | Being a newer technology, STARKs has less mature supporting libraries. Additionally, implementing the proof system can involve more complex details and require extra tooling. |
| Proof Size | Generally generate proofs that are smaller in size compared to STARKs. This can be advantageous for blockchains with limited block sizes, particularly on Layer 1. | While proof sizes are larger, they offer greater scalability, a crucial feature as Zero-Knowledge Proofs become more widely adopted within blockchain technology. |
| Trusted Setup | Require a trusted setup ceremony to generate initial parameters. Any vulnerabilities introduced during this phase can compromise the entire system’s security. | zk-STARKs helps eliminate the need for a trusted setup by offering a more secure and inherently trustless foundation. |
| Quantum Resistance | Rely on elliptic curve cryptography (ECC), which is considered vulnerable to potential attacks from sufficiently powerful quantum computers. | Utilize hash functions, providing a level of resistance against cryptanalysis by quantum computers due to their inherent one-way properties. |
| Use Cases | Privacy coins, ZK-rollups | Scalable computations, permissionless blockchain |