Introduction
Blockchain & Web3 Services Trusted By Leaders
- Develop innovative solutions using our state-of-the-art blockchain expertise.
- Achieve accelerated growth with robust & scalable Web3 consulting.
- Unlock 360-degree security with our top-rated blockchain development.
Permissioned vs Permissionless Blockchain: Comprehensive Guide
In this fast-paced technological era every day new innovations take center stage: one of the technologies is blockchain. It promises to revolutionize industries, enhance security, and redefine the way we conduct transactions. Real-life examples and applications with a lot of use cases for blockchain exist. But, within the world of blockchain, a fundamental question arises: What type of blockchain best suits your needs, let’s do a comparison —permissioned vs non permissioned blockchain? This comprehensive guide will help you delve deep into the distinctions, advantages, and applications of permissioned and permissionless blockchains. Whether you’re an enterprise owner seeking control and privacy or a startup, understanding these blockchain variations is vital for you. If you want to learn more about the evolution of blockchain and its transformative impact on the business landscape, explore our comprehensive blog on how blockchain supports sustainable business practices.
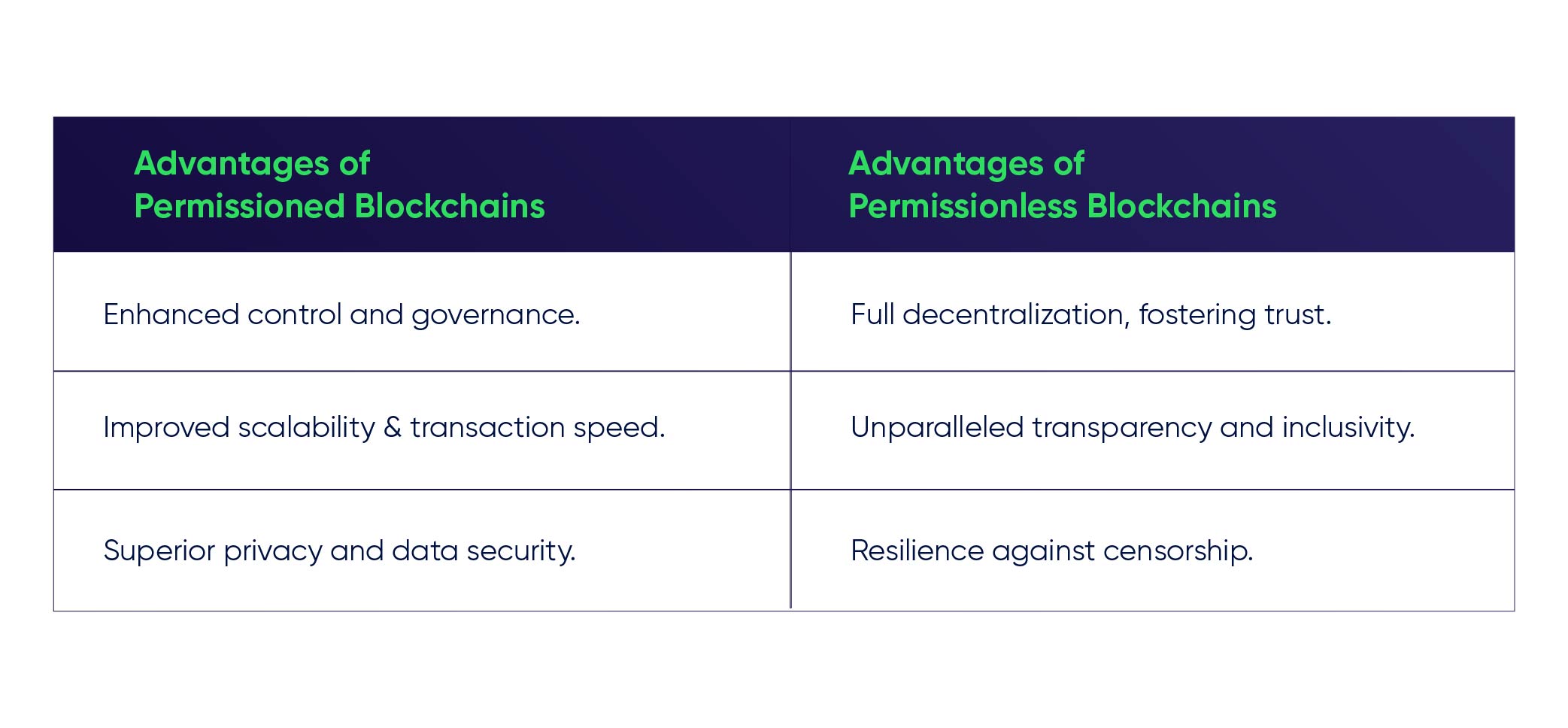
Permissioned vs. Permissionless Blockchain
As we all know Blockchain technology is promising unparalleled security, transparency, and efficiency. We will do a detailed comparison to help you decide but before going into details, let’s first establish a clear understanding of the blockchain concept.Permissioned Blockchain
A permissioned blockchain often referred to as a private blockchain is a type of network where access and participation are limited to a selected group of individuals. Moreover, permissioned blockchains operate with a controlled set of participants.Characteristics of Permissioned Blockchain
- Restricted Access: Private blockchain only allows participants that are authorized and identified in a Permissioned blockchain network. Also, access is limited to known and trusted participants, such as businesses, organizations, or consortium members.
- Centralized Validation: Permissioned blockchains often depend on a centralized authority or a specific group of validators to confirm transactions.
- Privacy and Confidentiality: Private blockchains often prioritize privacy and confidentiality. In addition, it allows participants to control who has access to view certain data on the network. This characteristic is typically important for applications in industries like finance and healthcare, where sensitive information must be protected.
- Scalability: Permissioned blockchain is more scalable than permissionless as they have fewer participants. Also, they can employ faster consensus algorithms which makes them suitable for enterprise applications with high transaction volumes.
- Use Cases: Private blockchains have many use cases in business and enterprise environments. They find applications in supply chain management, financial services, healthcare, identity verification, and more.
- Governance: There is a centralized governance in private blockchain which is under the control of the participating entities. It means that decisions about network upgrades and changes are made by a defined governance structure.

How Does a Permissioned Blockchain Work?
- Permissioned blockchains are managed by a central entity or a consortium of trusted organizations.
- Participants must be authorized by the governing entity to join the network.
- Participants on a private blockchain typically undergo identity verification before gaining access.
- Transactions on these networks are usually private and confidential.
- Permissioned blockchains often employ efficient consensus mechanisms like Raft.
- Permissioned blockchains are highly scalable due to fewer participants and controlled access, so they can possess transactions quickly.
Examples of Permissioned Blockchains and Their Uses:
-
Hyperledger Fabric
Hyperledger Fabric is a popular permissioned blockchain framework that was developed by the Linux Foundation. It is designed for enterprise applications and allows organizations to create private, customizable blockchains.
→ Use cases include supply chain management, healthcare data sharing, and financial services.
-
R3 Corda
Corda is a platform built for the finance industry to enable secure and efficient peer-to-peer transactions between financial institutions.
→ Corda is used for applications such as trade finance, identity verification, and cross-border payments.
-
IBM Blockchain
IBM offers a range of blockchain solutions, including permissioned networks tailored for various industries.
→ Used in supply chain management, food safety, digital identity, and trade finance
Permissionless Blockchain
A permissionless blockchain, also known as a public blockchain, is a decentralized digital ledger where participation is open to anyone without restrictions.Key characteristics of public blockchain
- Open Access: Permissionless blockchain is open to anyone with an internet connection and the needed software.
- Decentralization: Public blockchain depends on a distributed network of nodes (computers) to validate and record transactions.
- Transparency: Every transaction made on a permissionless blockchain is transparent and visible to anyone on the network resulting in accountability.
- Consensus Mechanisms: This kind of blockchain uses consensus mechanisms like proof-of-work (PoW), proof-of-stake (PoS), or others to validate transactions and secure the network.
- Incentivization: Miners on the public blockchain are usually rewarded with cryptocurrency tokens for their efforts in maintaining the network and validating transactions.
- Public Ledger: The transactions on the blockchain are public and can be audited by anyone.
- Use Cases: Public blockchains are commonly associated with cryptocurrencies like Bitcoin and Ethereum.
- Governance: Governance in permissionless blockchains is typically driven by the consensus mechanism and the community of participants.

How Does a Permissionless Blockchain Work?
- Anyone can participate in the network without requiring approval or permission from a central entity. So, the decentralization is a fundamental feature that ensures openness and inclusivity.
- Participants can join the network, validate transactions, and create new blocks without needing authorization. As a result, this openness fosters a sense of trust and transparency.
- While transactions are recorded publicly, the real-world identities of participants are hidden behind cryptographic keys. As a result, this pseudonymity offers a level of privacy while maintaining transparency.
- All transactions on a permissionless blockchain are transparent and visible to anyone on the network. As a result, this transparency is crucial for trust and security, as participants can independently verify the integrity of transactions.
- Permissionless blockchains commonly use Proof of Work (PoW) or Proof of Stake (PoS) consensus mechanisms. PoW requires participants, known as miners, to solve complex mathematical puzzles to validate transactions and create new blocks. PoS, on the other hand, relies on participants “staking” their cryptocurrency as collateral to participate in block validation.
- The security of permissionless blockchains is achieved through the decentralization of validators. No single entity has control over the network, making it resistant to censorship and attacks.
Examples of Permissionless Blockchains and Their Uses
-
Bitcoin
Bitcoin is a permissionless blockchain as it allows anyone to participate in the network, mine new blocks, and make peer-to-peer transactions.
→Its primary use case is as a decentralized digital currency and store of value.
-
Ethereum
Ethereum is another popular public blockchain that goes beyond digital currency. It enables the creation of smart contracts and decentralized applications (DApps).
→ Ethereum is used for applications such as decentralized finance (DeFi), non-fungible tokens (NFTs), and decentralized exchanges (DEXs).
-
Binance Smart Chain
Binance Smart Chain is a public blockchain that aims to provide fast and low-cost transactions.
→It is used for various DeFi applications, token creation, and cross-chain transfers.